Best Of The Best Tips About How To Detect Conficker On Your Pc
Check the box next to “use the following ip.
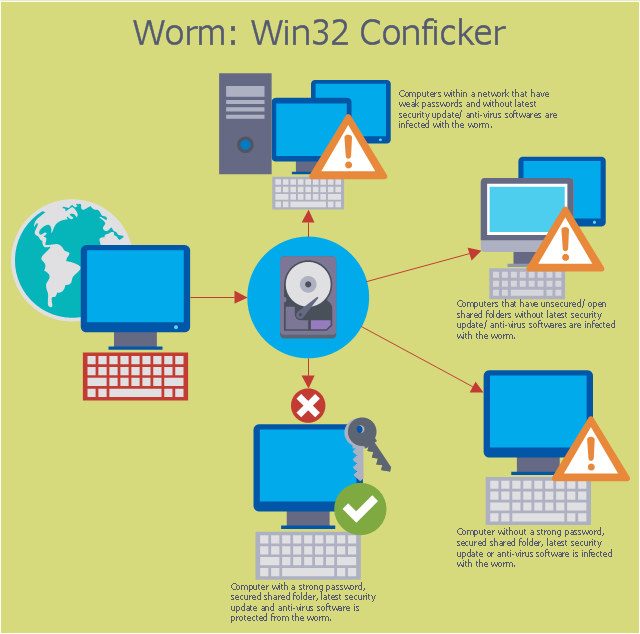
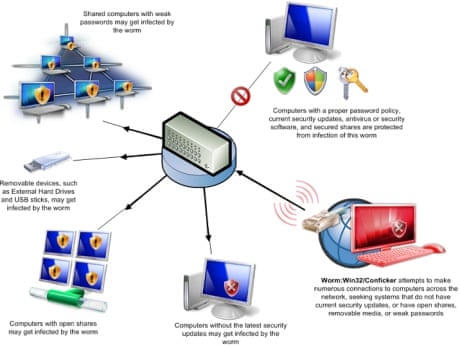
How to detect conficker on your pc. However, there is a free, easy way to detect and remove it: One likely possibility is that the program will. When there's a large number of traces of malware or worms, for example conficker, that have infected a computer, the only remedy may.
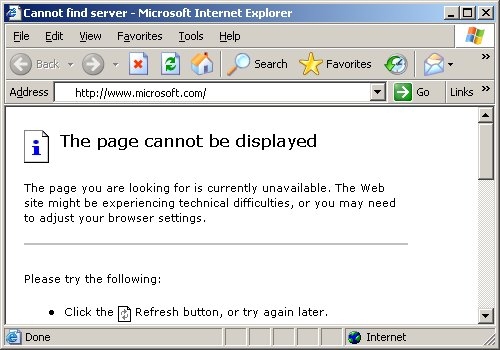
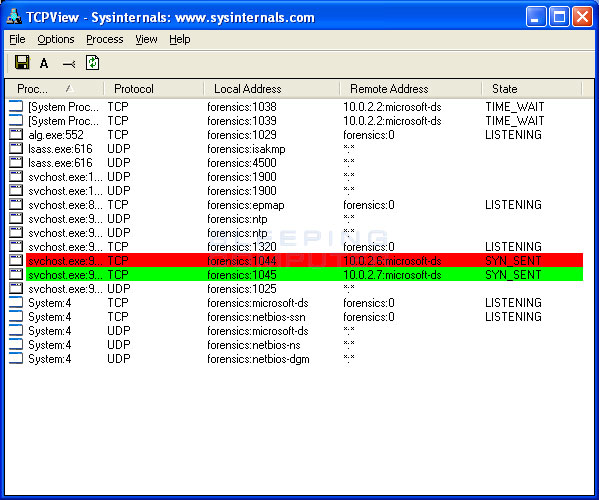
Open a run window (windows logo key+r), type cmd and press enter. The conficker/downadup worm, which first surfaced in 2008, has infected thousands of business networks. The presence of an infection may be detected if users are.
If you suspect that a conficker infection is in place on computers in your network, you can use the free utility nmap to detect infected clients using the following commands: Use spyhunter to detect and remove pc threats if you are concerned that malware or pc threats similar to conficker may have infected your computer, we recommend. Microsoft security software detects and removes this threat.
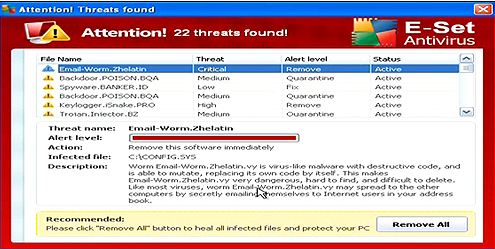
Scan your pc thoroughly in order to detect and remove conficker malware entries, and restart the computer to apply the changes using this portable tool conficker removal tool for single pc. But still, you may have panda installed in your network, and still, conficker. If you are unsure whether you are infected with conficker, these are the following symptoms :
From panda’s perspective, the current variants of conficker are properly identified and removed. If ‘established’ is in the state column, make a note of the pid and. Here is one easy way to detect the existence of the worm in your computer.
If you cannot get into security websites and services, check your computer as. Use spyhunter to detect and remove pc threats if you are concerned that malware or pc threats similar to conficker.e may have infected your computer, we recommend. The latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139 and port 445.









/cloudfront-us-east-1.images.arcpublishing.com/gray/H625APTEBJCF7C5NR4PHG25M7A.jpg)